
Understanding
Network visibility
See every single packet traversing your network
Learn about our other solutions for enterprise networks and data centers.
Optimize Network Performance
Improve network performance and reliability with APCON's tools and techniques.
Learn more
Ensure Regulatory Compliance
Meet compliance requirements while saving on monitoring costs with APCON's hardware.
Learn more
Enhance Network Security
Prevent breaches and ransomware and resolve problems faster with real time activity data.
Learn more
Empower Monitoring
Ensure the tools you rely on perform at optimal levels as your network fabric expands.
Learn more
real time insights
Network-wide packet-level visibility

APCON's aggregation and filtering solutions collect and send data to monitoring, performance, and security tools for faster insights.
APCON's all-in-one solution combines network visibility technology and third-party solutions for data centers, virtual machines, and cloud networks on one platform to help identify blind spots, bottlenecks, and potential performance issues to prevent threats to security and speed.
We continue to invest heavily in the advanced features and enhancements of our IntellaView visibility platform. IntellaView offers industry-leading port density, a flexible/scalable design that grows with your network, easy-to-use software management, and end-to-end visibility for today's hybrid networks.
Our solutions
How do you achieve total visibility?
IT and security teams use network or application performance and security analytics tools to gain network insights and act upon them. These devices rely on having complete and accurate access to all network traffic. Here's how APCON gets it done:
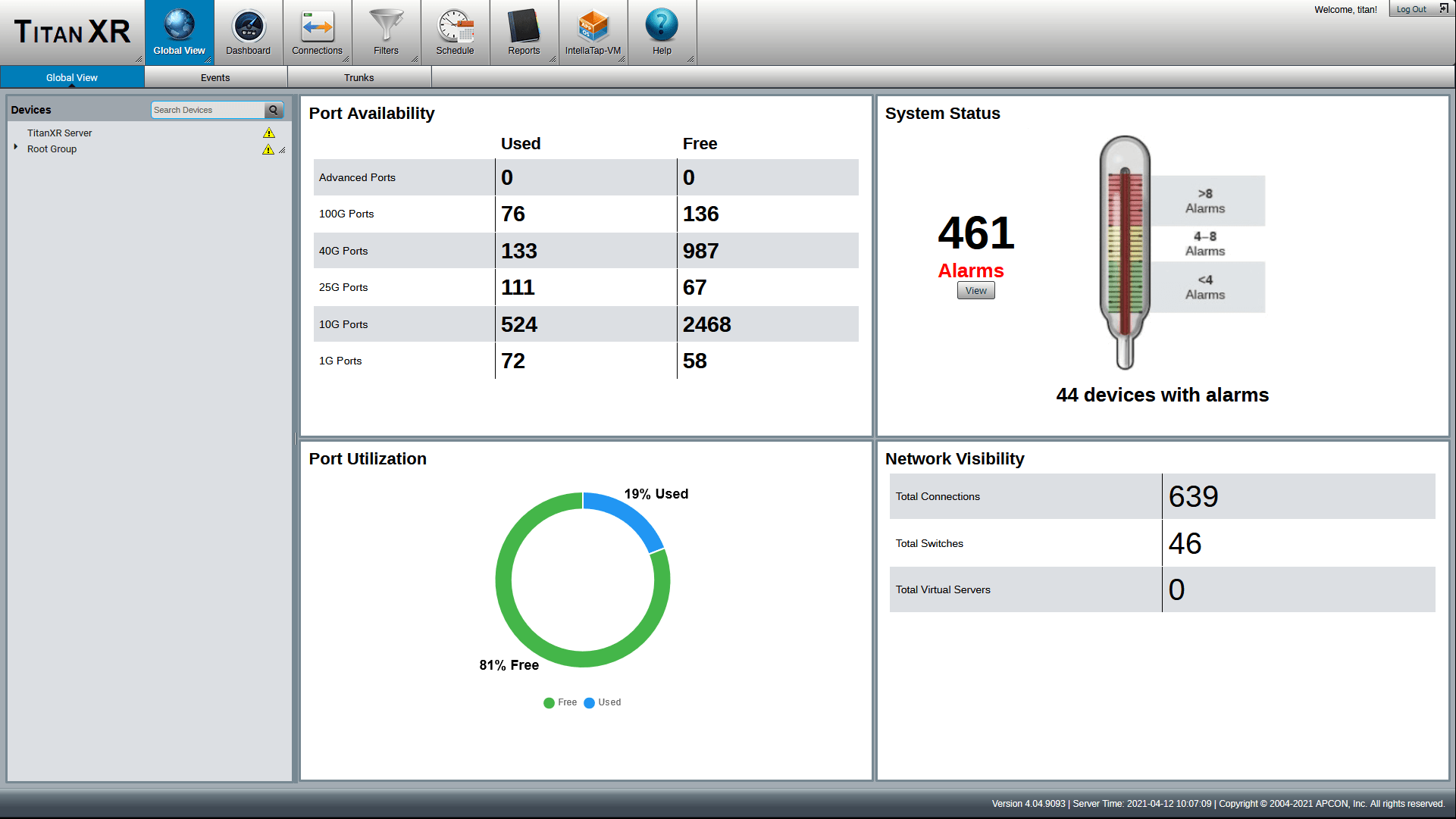
A single portal for your whole fabric
View all your network data and workloads, including system status and a summary of any events, with our browser-based IntellaView GUI. Save IT resources by notifying users of alert conditions, analyzing network traffic, scheduling and implementing firmware updates in batch mode, and managing users and connections.
Maximize your visibility.Get started today.
Ultra-high performance network visibility
The IntellaView Platform
Future-ready for hybrid networks
Get visibility for 5G mobile networks, IoT devices, video streaming, and data-intensive apps on-premises or in the cloud.
High-density design that scales
Get scale and investment protection with 1G / 10G / 25G / 40G / 100G high-density ports. A higher, full-featured, multi-speed port count gives you more visibility in a smaller form factor.
Eliminate cloud blind spots
Capture and monitor network traffic within your ever-expanding AWS cloud network.

Secure your hybrid data center with state-of-the-art visibility technology
Get the power to take your network's security, stability, and performance to the next level.
Application Filtering
Traffic classification and filtering based on protocol or application, automatically detecting over 1600 applications and 400 protocols in real time. Application Filtering can facilitate more efficient tool usage by filtering out low-risk traffic.
Learn more
Pattern Matching
Search on individual packets or sessions. This is useful for ensuring HIPPA compliance, masking PII such as credit card or social security numbers, and enabling more efficient tool usage by filtering out low-risk flows.
Learn more
Traffic Shaping
Limit Tx traffic to a user-specified average rate by buffering RX packets and transmitting them at steady, even flow. This is useful when tools are not able to handle traffic above a specific rate for extended periods of time.
Learn more
Deep Packet Inspection
Deep Packet Inspection (DPI) is used to monitor network traffic at the packet level to locate, identify, and classify packets of a specific type or those with a certain payload and react accordingly.
Learn more
Network Data Deduplication
Traffic Deduplication improves monitoring tool efficiency, accuracy, and recording space requirements. Enable your monitoring tools to provide greater visibility while lowering overall costs.
Learn more
Packet Filtering
Our unique Packet Filtering provides pinpoint accuracy in delivering data to your network monitoring and security tools, eliminating oversubscription of egress ports and resulting in zero dropped packets.
Learn more
Packet Slicing
By removing payload data from packets and leaving only the header information, network monitoring switches can send more data across any given link to performance and security monitoring tools.
Learn more
Protocol (Header) Stripping
Our advanced Protocol (Header) Stripping features (now including VN-tag and GENEVE stripping) ensure your diagnostic tools will have complete network visibility and operate at maximum efficiency.
Learn more
Tunneling
Tunnel Initiation & Termination services can be applied to ports so they can be used as tunnel sources or destinations, allowing for the transfer of packets from one network to another regardless of protocol.
Learn more
NetFlow Generation
Offload processing from routers and other production equipment to increase efficiency and save costs. Consolidate NetFlow sources to reduce network traffic and simplify your monitoring architecture.
Learn more
Secure your hybrid data center with state-of-the-art visibility technology
Get the power to take your network's security, stability, and performance to the next level.
Application Filtering
Traffic classification and filtering based on protocol or application, automatically detecting over 1600 applications and 400 protocols in real time. Application Filtering can facilitate more efficient tool usage by filtering out low-risk traffic.
Learn more
Pattern Matching
Search on individual packets or sessions. This is useful for ensuring HIPPA compliance, masking PII such as credit card or social security numbers, and enabling more efficient tool usage by filtering out low-risk flows.
Learn more
Traffic Shaping
Limit Tx traffic to a user-specified average rate by buffering RX packets and transmitting them at steady, even flow. This is useful when tools are not able to handle traffic above a specific rate for extended periods of time.
Learn more
Deep Packet Inspection
Deep Packet Inspection (DPI) is used to monitor network traffic at the packet level to locate, identify, and classify packets of a specific type or those with a certain payload and react accordingly.
Learn more
Network Data Deduplication
Traffic Deduplication improves monitoring tool efficiency, accuracy, and recording space requirements. Enable your monitoring tools to provide greater visibility while lowering overall costs.
Learn more
Packet Filtering
Our unique Packet Filtering provides pinpoint accuracy in delivering data to your network monitoring and security tools, eliminating oversubscription of egress ports and resulting in zero dropped packets.
Learn more
Packet Slicing
By removing payload data from packets and leaving only the header information, network monitoring switches can send more data across any given link to performance and security monitoring tools.
Learn more
Protocol (Header) Stripping
Our advanced Protocol (Header) Stripping features (now including VN-tag and GENEVE stripping) ensure your diagnostic tools will have complete network visibility and operate at maximum efficiency.
Learn more
Tunneling
Tunnel Initiation & Termination services can be applied to ports so they can be used as tunnel sources or destinations, allowing for the transfer of packets from one network to another regardless of protocol.
Learn more
NetFlow Generation
Offload processing from routers and other production equipment to increase efficiency and save costs. Consolidate NetFlow sources to reduce network traffic and simplify your monitoring architecture.
Learn more
